Module Information Structure (MIS) Resources
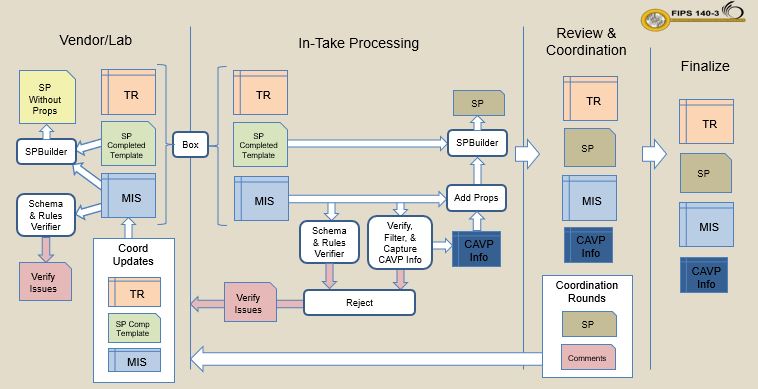
To facilitate automated verification and processing of the modules, much of the information needs to be submitted in a structured and organized format. The CMVP uses JSON as the submission format to provide a mechanism for receiving this structured data. The information below describes the JSON structure and programs the CMVP provides to create and verify the JSON. This JSON file is referred to as the MIS.
Important Note: Because of the potential of changes in the _module.json schema related to different versions of Web Cryptik Br1, it is important to use the ModVerifyApp program to Select, Load and Update, and Save previously generated _module.json files before importing them into Web Cryptik Br1. Web Cryptik is not able to upgrade schema and even with editing and saving, will perpetuate schema errors into newer versions.
Security Policy
The Security Policy is one of the required documents. To eliminate duplication of information and the need to verify two separate sources, several fields and tables within the Security Policy are populated with information by the CMVP after the module package is submitted. The field and table information source is the MIS. The other information is entered by the vendor into a copy of the CMVP supplied Microsoft Word template document (link below). This completed template is merged with the MIS fields and tables to produce the final Security Policy. The CMVP has provided a program (link below) that performs that information merge so that the vendors and labs can see what the final Security Policy will look like.
Process Support Applications
- Web-Cryptik
- MIS Verifier and Security Policy Builder